Defending Against DDoS Attacks: Practical Strategies for Every Business
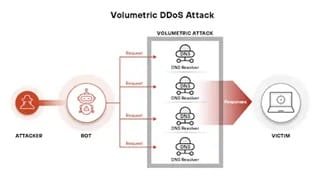
Table of Contents
- What DDoS Attacks Look Like Today
- Key Signs of an Incoming Attack
- Why DDoS Attacks Are on the Rise
- Real-World Consequences for Companies
- DDoS Mitigation: Best Practices
- Choosing the Right Mitigation Tools
- The Role of Cyber Readiness Training
- Industry Trends in DDoS Defense
- Future-Proofing Your Network Defenses
- Additional Resources and Research
What DDoS Attacks Look Like Today
DDoS attacks have evolved from simple assaults to sophisticated threats, using various techniques and botnets of compromised devices. They overwhelm targets with vast volumes of malicious traffic, often combining volumetric and protocol attacks. Organizations are now targets, not just corporations or government agencies. Attackers exploit vulnerabilities in network infrastructure and web-facing applications, leaving businesses vulnerable without warning. Many companies are turning to DDOS protection solutions as a foundational defense. These services work by analyzing incoming traffic, scrubbing malicious packets, and only permitting legitimate data through to the business’s network—helping to prevent crippling outages that can lead to both revenue loss and reputational harm.
Key Signs of an Incoming Attack
Recognizing a DDoS attack in its early stages is essential for mitigation. While some disruptions may appear as just another technical hiccup, there are specific patterns that signal something more sinister. For instance, a sudden and unexplained spike in network traffic, particularly from unusual geographic regions or unknown sources, should raise red flags. Users may report slow website performance, frequent disconnections, or complete website outages. Simultaneously, IT teams might notice CPU or memory resources on servers being exhausted without explanation.
- Frequent, repeated timeout errors for users and internal systems
- Significant increase in bandwidth usage outside regular business hours
- Floods of requests to a specific page or application endpoint
- Anomalies of repeated error messages in system logs and dashboards
Businesses can more rapidly detect deviations by establishing clear baseline metrics for “normal” traffic. Technologies such as intelligent firewalls and intrusion detection systems help monitor these metrics and auto-alert teams at the first sign of trouble. Speed in identifying an active attack is critical, allowing a rapid response before it escalates.
Why DDoS Attacks Are on the Rise
The proliferation of DDoS attacks globally has been well documented, and for good reason. This trend contributes to the ease with which almost anyone, regardless of technical ability, can rent a DDoS-for-hire service or purchase an attack toolkit from illicit online marketplaces. This accessibility has lowered the barrier to entry for would-be attackers, making DDoS an option for cybercriminals, hacktivists, and unscrupulous competitors. As digital services become central to companies’ business, attackers see more opportunities to cause damage, extort businesses, or make political statements. Sometimes, DDoS attacks are launched to cover more targeted data breaches or ransomware campaigns. According to the Akamai DDoS attack trends report, 2023 saw an increase in attack frequency and size, with some incidents peaking at several terabits per second. This shows just how powerful and destabilizing these attacks can be.
Real-World Consequences for Companies
The business impacts of a DDoS attack can be drastic and far-reaching. Immediate effects include website downtime, lost e-commerce transactions, and interrupted access to critical services for employees and customers. But the costs rarely end there—extended outages can erode user trust, attract negative media scrutiny, and encourage regulators to take note. For instance, when a European financial institution suffered a sustained DDoS event, it lost revenue, decreased customer satisfaction, and experienced regulatory review. Financial losses can be staggering. Industry studies estimate that downtime from such attacks can cost larger organizations over $5,000 per minute, factoring in lost sales, emergency IT resources, and brand recovery efforts. Small- and medium-sized businesses face even higher risks relative to their resources, with some going out of business following a major attack. These case studies show why resilience and swift response are vital in the modern business climate.
DDoS Mitigation: Best Practices
A well-prepared organization will have layers of defenses to reduce its DDoS risk. Effective strategies begin with network and application monitoring, using automated systems that promptly recognize suspicious patterns and alert administrators. Developing an incident response plan outlining who is responsible for different aspects of the response and how communications should be handled internally and externally is essential.
- Monitor network and application performance using real-time analytics
- Audit and update your DDoS response plan after every tabletop exercise or incident
- Limit unnecessary open ports, filter unwanted traffic, and implement rate limiting where appropriate
- Keep all network hardware and software patched to close off vulnerabilities
- Consider partnering with a dedicated mitigation provider for added detection and defense
Practicing your response plan, not just writing it, separates organizations that recover swiftly from those left scrambling during an attack.
Choosing the Right Mitigation Tools
Finding the right tools and services to protect against DDoS attacks can be daunting, but certain principles help guide effective choices. A common approach is to deploy a combination of hardware and cloud-based solutions: firewalls for perimeter defense, web application firewalls for application-level threats, and cloud-based scrubbing centers for volumetric attacks. This comprehensive setup increases the odds of stopping an attack before any real disruption occurs. Thought leaders and analysts agree on the power of a layered defense. Supplementing traditional security appliances with adaptive solutions that leverage artificial intelligence and automation offers a better chance at real-time detection and mitigation. Companies that regularly assess their network architecture and upgrade their protection see measurable improvements in resilience.
The Role of Cyber Readiness Training
Technical controls alone aren’t enough; employees at every level have a role to defend the organization. Regular, role-specific cyber readiness training builds a culture of vigilance. Companies should run annual tabletop exercises that replicate realistic DDoS scenarios. These drills help teams practice the response, revealing gaps or inconsistencies before a real attack happens.
- Practice communication protocols and escalation paths with all departments
- Review lessons learned after each training or incident and update procedures accordingly
- Offer basic cybersecurity awareness training for all staff—not just IT—so they can recognize early warning signs
Organizations investing in people and technology are poised to survive and recover from disruptive events.
Industry Trends in DDoS Defense
DDoS defense is evolving quickly. New solutions leverage artificial intelligence and behavioral analytics to spot abnormal traffic patterns as early as possible. Machine learning algorithms, for example, analyze billions of network transactions to distinguish between legitimate user activity and attack traffic, often well before human analysts spot the difference. Collaborative initiatives are increasing industry-wide. Threat intelligence sharing between organizations and agencies accelerates the learning curve, preparing companies for evolving threats. Public-private partnerships are also vital, as infrastructure providers and government bodies join forces to bolster defenses for critical infrastructure across sectors.
Future-Proofing Your Network Defenses
Keeping your network safe isn’t a one-time exercise. Future-proofing involves regular vulnerability assessments, penetration testing, and adopting zero-trust principles. In this concept, no device or user is trusted by default, reducing the risk of compromised accounts or devices. Security policies should require continuous authentication and least-privilege access across the organization. As DDoS attackers adapt, more companies are adding cybersecurity insurance to their strategies, safeguarding themselves financially should an attack succeed. This, combined with proactive defense measures, ensures that organizations remain resilient and adaptive as cyber threats continue to change.
Additional Resources and Research
Anyone tasked with protecting business operations must stay informed on the latest DDoS trends, technologies, and real-world incidents. Use annual threat reports published by industry leaders, subscribe to reputable security blogs, and participate in cybersecurity forums. Regularly reviewing white papers, best practice guidelines and case studies from trusted authorities can equip teams to better understand and tackle evolving DDoS tactics. As cyber threats continue to escalate, a proactive and informed approach will position organizations to defend against not only today’s attacks but also tomorrow’s emerging risks.



